Insights - 6 | 12 | 17 | 10
It is now 4 months ago that we maintain our fork. And we are very proud of what we have achieved since then.
The numbers in the headline are describing the activities of the last weeks since our last release: 6.0.33.
- 6 contributors
- 12 new GitHub stars
- 17 merged pull requests
- 10 active issues
Even at the forum we got more and more active users and an increasing amount of new posts.
Life is returning to the community, after years not being able to actively participate in this open-source project.
It is now 4 months ago that we maintain our fork. And we are very proud of what we have achieved since then.
The numbers in the headline are describing the activities of the last weeks since our last release: 6.0.33.
- 6 contributors
- 12 new GitHub stars
- 17 merged pull requests
- 10 active issues
Even at the forum we got more and more active users and an increasing amount of new posts.
Life is returning to the community, after years not being able to actively participate in this open-source project.
We thank you and do our best to keep it that way. Keep up the good work.
Fixed XSS 6.0.34 and security in general
As already written several times, we're reviewing the existing code.
This is done by checking one component after the other and not the complete application at once.
And to be honest, it is too much to do this at once.
Right now we are searching for security auditors who are able to understand der Perl code and all it's dependencics. We like to go beyond a default audit.
As soon as we found a reliable partner for this task we will contract for an external, independent audit.
In the meantime we got help from individual security analysts, through tips from other projects and through our own research.
These own researches often result from bug reports, which we then look at in detail during the root cause analysis.
The current version 6.0.34 closes an XSS vulnerability. It existed there for quite some time and and as far as we can tell also exists like this in the OTRS 7 code base.
This vulnerability was discovered by a university's bug report and was initially not related to any kind of security.
This bug report was intended to find out why some e-mails created error messages in the web server's log.
Our root cause analysis and experience in this area
quickly led us to a possible XSS vulnerability.
A few hours later, we had a complete proof-of-concept to:
- reading customer data
- sending e-mails
- adding users, changing settings if a user has admin permission
This specific gap doesn't need any user interaction at this point.
In fact, you can make it so good that not even the relevant ticket appears in an overview.
Just looking at the queue where the ticket is located is enough.
Many users don't see XSS as a real threat. But we like to point out: it can be and you should take it seriously.
We are actually asked why we release security fixes so often.
It's not the software that is not bad and the programmers aren't either.
But technologies change, vectors for attacks change, and mistakes happen.
We take these facts into account through our regular updates.
Updates from the engine room
Over the last weeks, our team, specifically Denny Korsukéwitz, Roy Kaldung and help from b1-luettje have been activating and configuring the CI environment at GitHub.
Since the end of March, most of the unit tests and our code policy are now running on GitHub.
This allows us to evaluate changes to the code directly and also provide direct feedback to external contributors on their pull requests.
One part of the Selenium tests remains open at the moment, and we are still working on it.
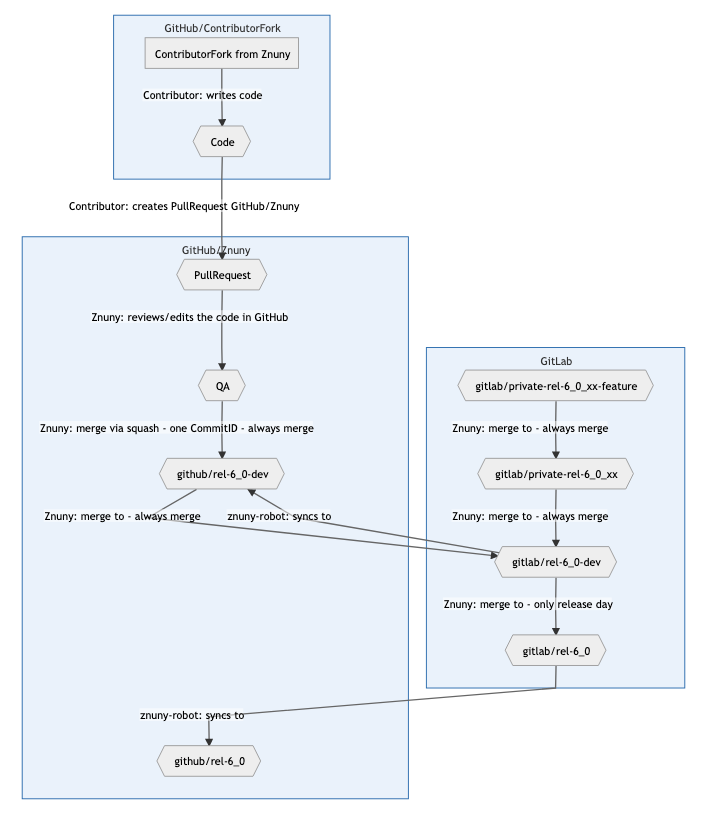
We also changed the synchronisation from our internal GitLab to GitHub.
In the beginning, we had an internal GitLab branch that was not synced directly to GitHub. This resulted from the time pressure we had to take over the fork. However, this brought us more and more disadvantages as time went on. For example, commit IDs no longer fit and the code had to be synchronized several times.
As a result, we changed our setup and can now keep everything in sync and still merge and release cleanly.
The branch rel-6_0-dev on GitHub is always in sync with our branch rel-6_0-dev in GitLab. When a release cycle is over, this branch is merged with rel-6_0 and pushed to GitHub.
Now that everyone is working with the rel-6_0-dev branch or a copy of it, it makes our job much easier.
What's next
At the moment a web agency updates our project's website www.znuny.org. The current version works, but is only a stopgap.
If everything works out the new site will be online at the beginning of May.
There will also the roadmap for the planned version with new features. An explanation how we envision the future of the product and what the differences between the versions will be
An explanation of how we envision the future of the product and what the differences between the versions will be complete the roadmap.
Your Znuny Team
